Nine things a government agency may not be destroying but should be
 As computers and other electronic devices become obsolete sooner and sooner due to new technology, disposal of sensitive information is of serious concern. A single used hard drive, CD or DVD can contain thousands of files. When a digital file is “deleted” from a computer, the information actually remains on the hard drive, as do deleted e-mail messages and records of all online activity. These days, it all can be recovered with sophisticated tools.
As computers and other electronic devices become obsolete sooner and sooner due to new technology, disposal of sensitive information is of serious concern. A single used hard drive, CD or DVD can contain thousands of files. When a digital file is “deleted” from a computer, the information actually remains on the hard drive, as do deleted e-mail messages and records of all online activity. These days, it all can be recovered with sophisticated tools.
In addition to identity thieves, “dumpster divers” can obtain proprietary information from items that are merely discarded instead of thoroughly destroyed.
The following chart lists some items that could cause problems if not disposed of properly but can be rendered harmless by one or more of the following methods:
- Shredding — Reducing items to small strips/particles.
- Degaussing — Using powerful magnets to permanently eliminate data from magnetic media.
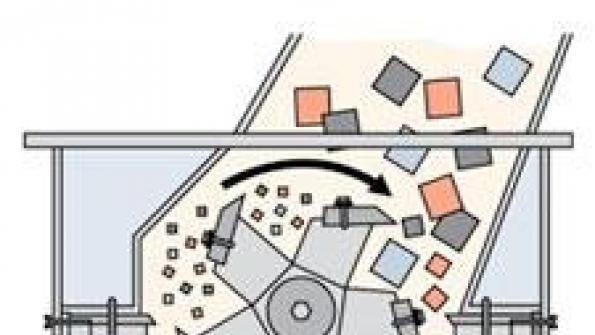
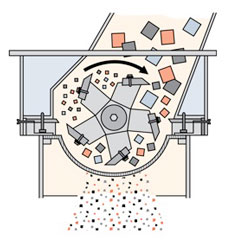
- Disintegration — “Mechanical incineration” that continually cuts items into small pieces until they are unrecognizable and unreconstructible.
- Declassification — Physically grinding the data-bearing surfaces from CDs and DVDs.
- Crushing — Destroying hard drives by subjecting them to extreme pressure from a conical steel punch or similar device.
1. Item: Computer hard disk drives
Threat: Data theft — documents, spreadsheets, databases, etc.
Destruction method: Shredding, crushing, disintegration or degaussing
2. Item: Thumb drives/flash drives/memory cards
Threat: Data theft — Documents, spreadsheets, databases, etc.
Destruction method: Shredding or disintegration
3. Item: Cell phones/BlackBerries & other PDAs
Threat: Data theft — Contact lists, call logs, images, etc.
Destruction method: Shredding, crushing or disintegration
4. Item: Optical media — CDs/DVDs
Threat: Data theft
Destruction method: Shredding, disintegration or declassification
5. Item: Other magnetic media — Floppy disks, Zip disks, computer backup tapes
Threat: Data theft
Destruction method: Shredding, disintegration or degaussing
6. Item: Expired inventory, off-spec products, prototypes
Threat: Data theft — Corporate liability, brand degradation, industrial espionage
Destruction method: Disintegration
7. Item: Credit cards/ID badges
Threat: I.D. theft — Data on magnetic strip
Destruction method: Shredding (paper shredder OK for low volume) or disintegration (high volume)
8. Item: Audio, video & micro cassettes
Threat: Data theft — Meeting records, sales aids/training materials
Destruction method: Disintegration or degaussing
9. Item: Laser printers & fax machines
Threat: Data theft — Remnant data on drums & internal memory
Destruction method: Shredding or disintegration
Government agencies and other organizations that cannot afford to purchase destruction equipment for the relatively few items they need to destroy may choose to outsource such destruction. If an organization chooses to outsource, it should learn just how secure the destruction facility is. Here are some questions to ask:
1. How are materials transported to the destruction facility? Does the facility offer locked, trackable transport cases?
2. Does the facility require service contracts or monthly minimums?
3. Upon arrival at the facility, will the items be inventoried and stored in a locked area?
4. Are job applicants thoroughly screened? Is the facility monitored around the clock by security cameras?
5. What destruction methods will be used? The facility’s equipment should turn everything into “E-scrap” — tiny, unrecognizable fragments.
6. Has the facility’s equipment been approved by the U.S. National Security Agency?
7. Will the destruction of the items be certified in writing?
8. What happens to destroyed waste? Is any of it recycled in accordance with pertinent regulations?
9. Is the facility bonded and insured?
If the agency does not like the answer to any of those questions, it should look for another facility.
Andrew Kelleher is president of Westboro, Mass.-based Security Engineered Machinery (SEM), a direct supplier of high-security information destruction equipment to the federal government and its security agencies. The company also sells information destruction equipment to state and local agencies, and operates a full-service destruction facility. For more information, contact Kelleher at SEM, PO Box 1045, Westborough, MA 01581, TEL: 508-366-1488, FAX: 508-366-6814, e-mail: [email protected].
An association that can provide more information is the National Association for Information Destruction.